Whether you run a single-page brochure or business card style website, a thriving e-commerce store, or a WordPress blog focused on your favorite hobby, website security is a must. Even the most veteran of web developers can overlook common website security techniques, especially if budget and time constraints are limited. This web dev tutorial will walk you through some basic – yet often overlooked – elements of a secure website. If your site does not have these website security must-haves, be sure to get them added as soon as possible.
Website security is important for a number of reasons. For starters, having a site that is not secure can cause malware and viruses to spread to anyone visiting your page (including yourself) and can lead to identity theft, data privacy issues, and malicious malware or ransomware. Flaws in web security can also lead to website downtime, loss of revenue, loss of customer trust, and even affect your search engine optimization or ranking in the search engine results pages (SERPs).
Website Security Best Practices for 2021
The following website security tips can be applied whether you own a website built on a Content Management System (CMS) – such as WordPress, Drupal, or Joomla – or a custom site built using HTML, JavaScript, and CSS. Even websites built with web frameworks like Django or commercial platforms like Wix or Shopify can benefit from these security suggestions.
Install a Web Application Firewall
Web application firewalls (WAFs) are a type of application firewall used to block, filter, and monitor HTTP traffic directed to a website and from a website. Web app firewalls inspect incoming and outgoing traffic to help prevent malicious attacks aimed at exploiting common or known exploits in a web app using techniques such as cross-site scripting, file inclusion, and SQL injection – to name but a few.
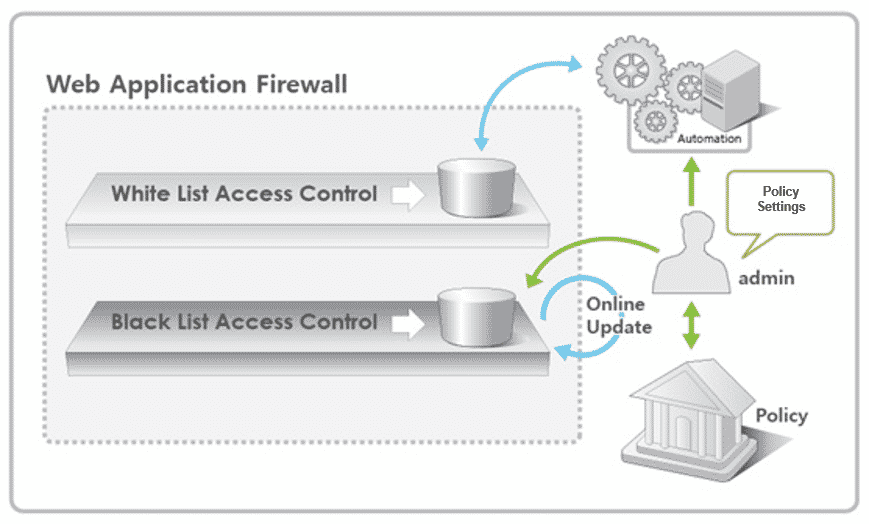
Popular choices for web application vendors include Barracuda Networks WAF, Citrix Netscaler Application Firewall, Fortinet FortiWeb, Qualys WAF, and Imperva SecureSphere.
Cloud options exist as well, including popular WAF offerings like Amazon Web Services (AWS WAF), CDNetworks, Cloudflare, Microsoft Azure Application Gateway with WAF, Succubi, and VMware.
Open Source web application firewalls exist as well. They include choices like ModSecurity, WebKnight, and Shadow Daemon.
Two-Factor Authentication (2FA)
If you allow user logins on your website or user accounts, you should consider requiring Two-Factor Authentication – or 2FA. 2FA is a process whereby users must use two different factors to authenticate their username prior to logging in or accessing your sites. Types of authentication begin with a password and then use a second process such as answering a puzzle, receiving a text with a special code, or even more complex forms of authentication like fingerprint scanning.
In addition to requiring Two-Factor Authentication, you may as well also require users to create strong passwords. Strong passwords consist of a combination of uppercase and lowercase letters, numbers, and special characters (@#!$%&, etc.). Since these types of passwords can be difficult to remember, consider having employees or those with access to your site use a password solution like LastPass.
Finally, be sure to remove any default account that is not actively used and, at the very least, change the default password. When employees leave your company, or if they move to a different department where they no longer require access, be sure to remove their old access as well.
Install an SSL Certificate
SSL Certificates – or Secure Sockets Layer certificates – are not just for e-commerce websites. They are for any site that has sensitive information – including usernames, passwords, credit card information, client addresses, emails, and so forth. SSL certificates work by turning your HTTP sites into an HTTPS secure website. This is achieved by means of encryption; all data on your website will be encrypted and, therefore, less vulnerable to exploitation.
Another good reason to get an SSL Certificate for your website has to do with search engine optimization. Google looks more favorably on secure websites, and it also helps you avoid getting the Google “unsafe website” warning. You can get SSL certificates, most commonly, from your hosting company, such as GoDaddy or BlueHost.
Update Websites Frequently
If you run a website using a content management system like WordPress, make sure that you update your version of WordPress Core when updates become available. The same can be said for plugins, themes, extensions, and so on. If you have themes or plugins that have not been updated in a long time, consider removing or replacing them with a similar option. Likewise, if you want to install a plugin, make sure that it has been downloaded a good amount of times, that it gets updated frequently, is supported by its developer, and that it works with the latest version of WordPress or whichever CMS you are using.
Hackers look for plugins, extensions, themes, and CMS cores that are not updated to take advantage of known exploits. Updating these resources can help limit a hacker’s ability to infiltrate your website.
This is not just limited to websites that run on content management systems, either. Updating to the most recent version of PHP, for instance, can also help reduce vulnerabilities.
Change Default Configurations
Cybercriminals and hackers often rely on bots to find common vulnerabilities in websites. One area that is often overlooked by even the most seasoned of web developers is the default configuration security settings of their sites. Once a bot finds these settings, it can use them to gain access to your files, where they can further change things like file permissions, read/write permissions, comment settings, user controls, and a host of other settings that expose user information and add access.
Monitor and Backup Websites
Using tools to monitor access to your website, file changes, and the like are crucial to the security of your website. This is known as continuous monitoring in the security world. Continuous monitoring security software looks for signs that indicate your website security may have been breached and notifies security teams. Signs of a security threat include changes in user accounts, modification, deletion, and addition of files without the web developer’s knowledge, website performance issues, rapid increases or decreases in traffic, and warnings from Google concerning harmful content or being blacklisted.
Once detected, solutions can be deployed, such as scanning files, removing them, and changing permissions. Another benefit to website security monitoring tools is that you can have them scan your website files for known vulnerabilities and flaws in your security setup. This is an invaluable tool because it can help you fix problems before they become a major issue.
Finally, one of the most important security measures you can take is to back up your website files frequently. In the event that you cannot recover your website or need to roll it back to an earlier version, a backup will be your best friend. If you run a website on a CMS, there are plenty of backup plugins available. For non-CMs websites, you can back up files via FTP or other website backup tools.